
Following the encryption debate surrounding the San Bernardino shooter's iPhone and increasing concerns over "digital strip searches" at the U.S. border, more and more people are paying attention to the data on your phone. From the police or border agents that may seek to see who you've been communicating with, to hackers and malware-makers that want to exploit vulnerabilities in your software or hardware to steal your identity or photos, and corporations like Google and others that simply want to keep tabs on everything you do, the data on your smartphone is more precious than it has ever been.
Sometimes you need an exact copy of the data on your phone so you can work with the copy and leave the original untouched. One such time is during a digital forensic investigation, where the data's integrity is vital. Another is when you want to work on corrupted or infected data without worrying about further damage to the data. In both cases making an exact copy of the data and using the duplicate is essential. The process of duplicating the data is the same too.
Sometimes you need an exact copy of the data on your phone so you can work with the copy and leave the original untouched
Today we're going to explore how the process of data acquisition works and what can be done with it. Data acquisition for an Android device is split into two categories; internal storage and external storage. Data acquisition techniques can be broadly categorized into three distinct types: Manual, Physical, and Logical Acquisition which we will delve into below.
The guide will put you in the shoes of those acquiring data from an SD card and show you how an image is created before it's ready to be forensically analysed. Knowing how it works may help you protect yourself and your data in future, but it's also just plain fascinating.
Manual Acquisition
During a manual data acquisition, the forensic examiner will use the electronic device as normal and access stored data through its user interface. The examiner will then take pictures of the screen of all the data present on the device, to potentially be used as evidence further down the line. This procedure requires very few resources and needs no external software. Its main disadvantage is that only data visible through the device itself is accessible by the examiner. Any data that might have been deleted or purposely hidden will be harder to find, due to the the examiner being only view data through the device's user interface.
Physical Acquisition
A physical acquisition involves a bit-for-bit replication of an entire physical data store. By accessing the data directly from the flash memories, this technique allows for the extraction and reconstruction of deleted files and data remnants during the data analysis stage. This process is more difficult than manual acquisition because every device needs to be made secure against unauthorized access to memory. Digital forensic tools can aid this process by enabling access to memory, allowing examiners to bypass user pass codes and pattern locks.
Logical Acquisition
Logical extraction acquires information from the device using the original equipment manufacturer's application programming interface to synchronize the phone's contents with a computer. The recovered data is preserved in its original state with forensically-sound integrity and therefore could be used as evidence in court. One advantage of a logical acquisition is that the data is easier to organize, as it images the data structure within the system. Call and text logs, contacts, media, and app data present on the device can be extracted and viewed in their respective tree structures. Unlike a physical acquisition, logical extractions will not recover deleted files.
In modern mobile devices, memory is split between internal and external storage. A lot of data lives on SD cards, giving users the chance to increase the overall storage of their device. For forensic examiners, SD cards represent another form of storage which requires both acquisition and analysis in order to form a holistic digital investigation. In the walkthrough below, there is a step-by-step guide on how to create a physical image of an SD card. Following the successful imaging of the memory card, the data can be analyzed using traditional forensic analysis tools.
Physical Imaging of an SD Card using FTK Imager software
- Launch FTK imager (can be downloaded from here).
- Safely remove the SD card from your Android device and insert it into your PC.
- Navigate to File — Create Disk Image

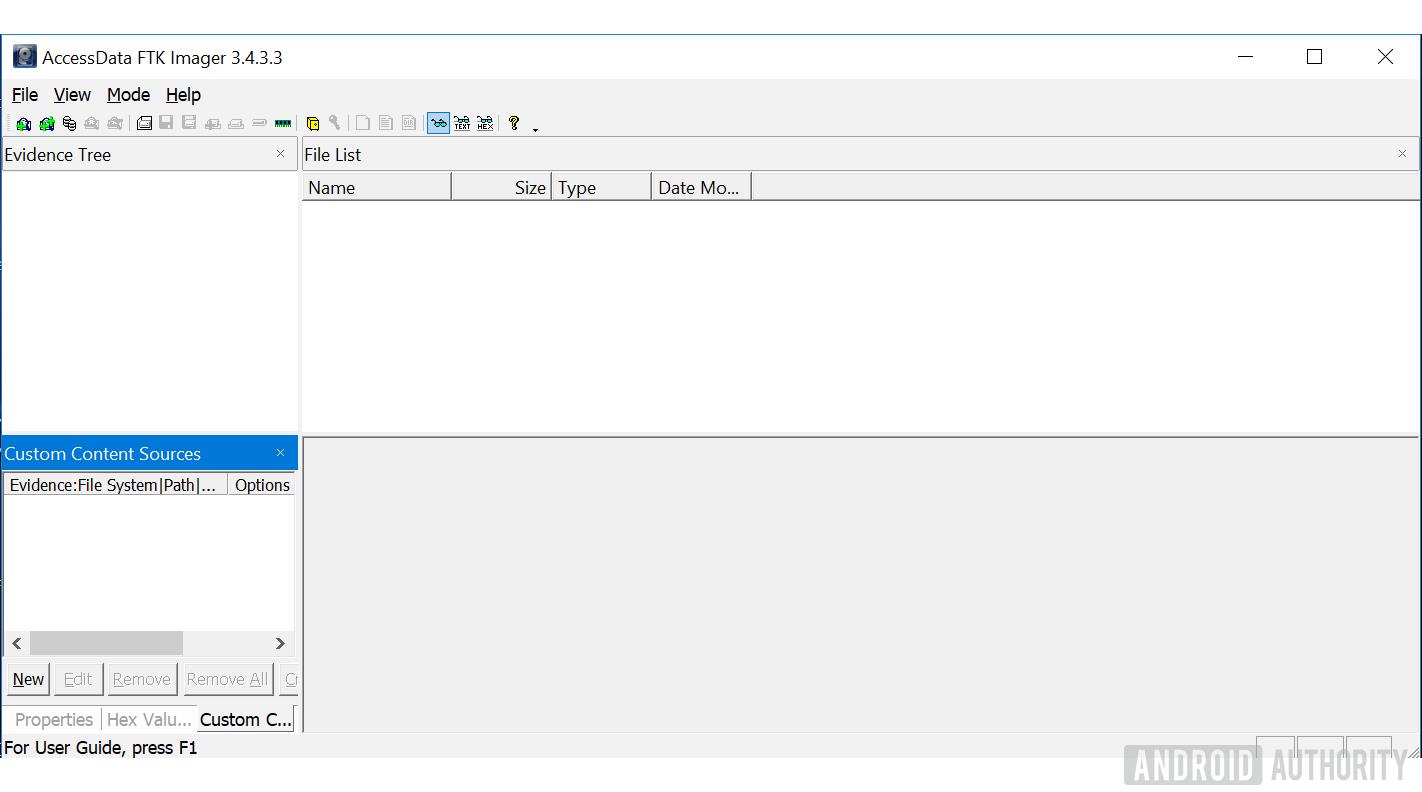
- A new pop up window will ask you to select type of acquisition, select "Physical Drive."
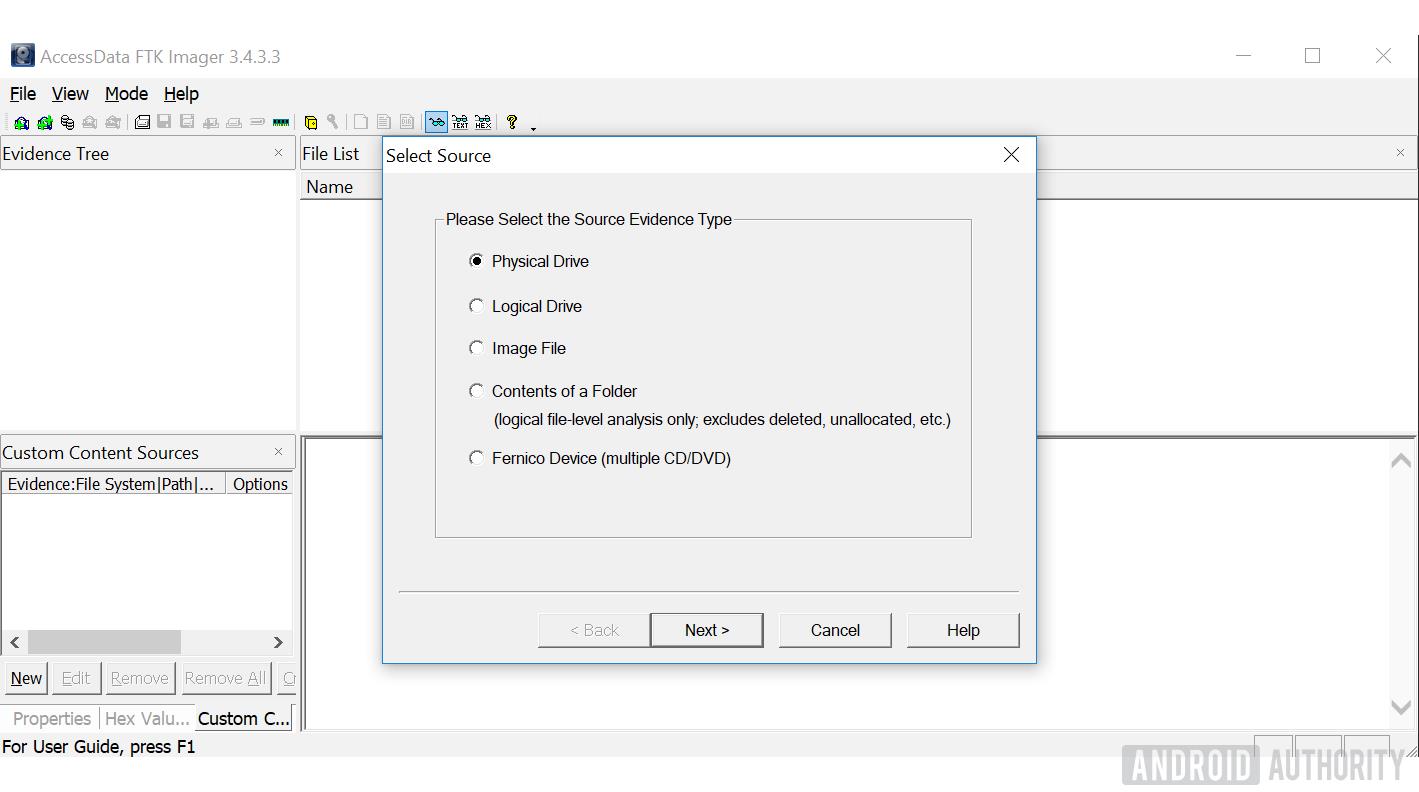
- Select the SD card from the Source Drives dropdown list.
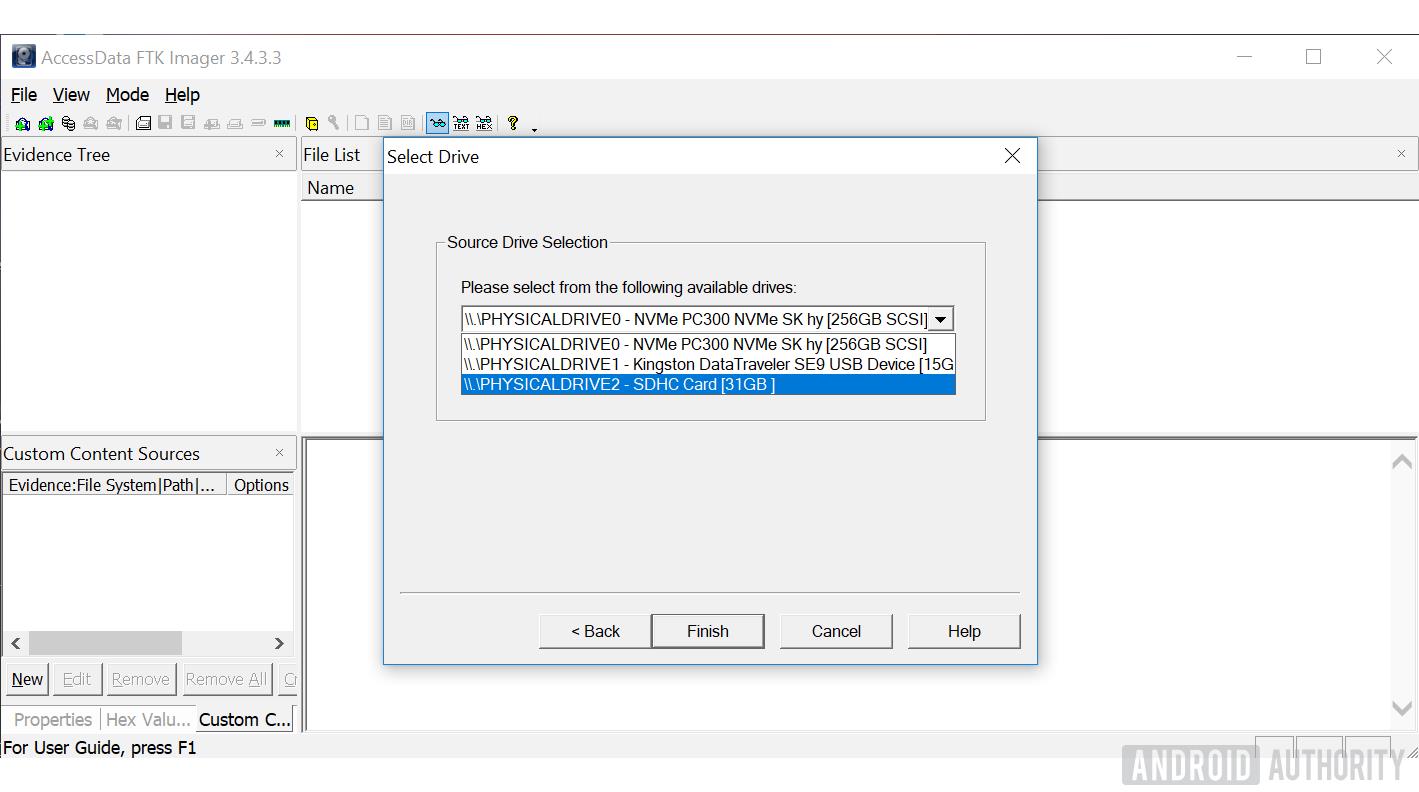
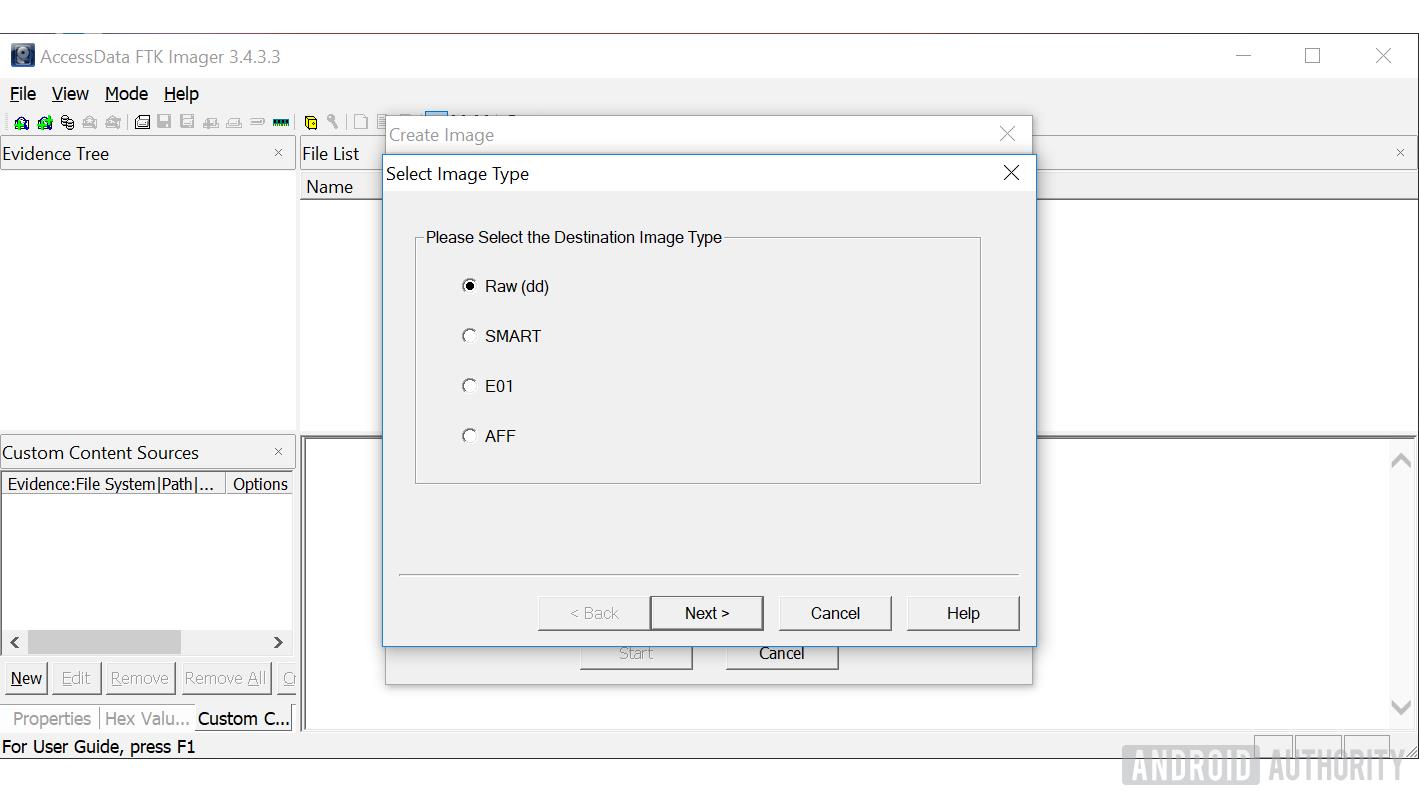
- In the "Create Image" window select "Add" and select the Destination Image Type "Raw (dd)."
- Fill out the "Evidence Information" section with appropriate information or skip by pressing next.
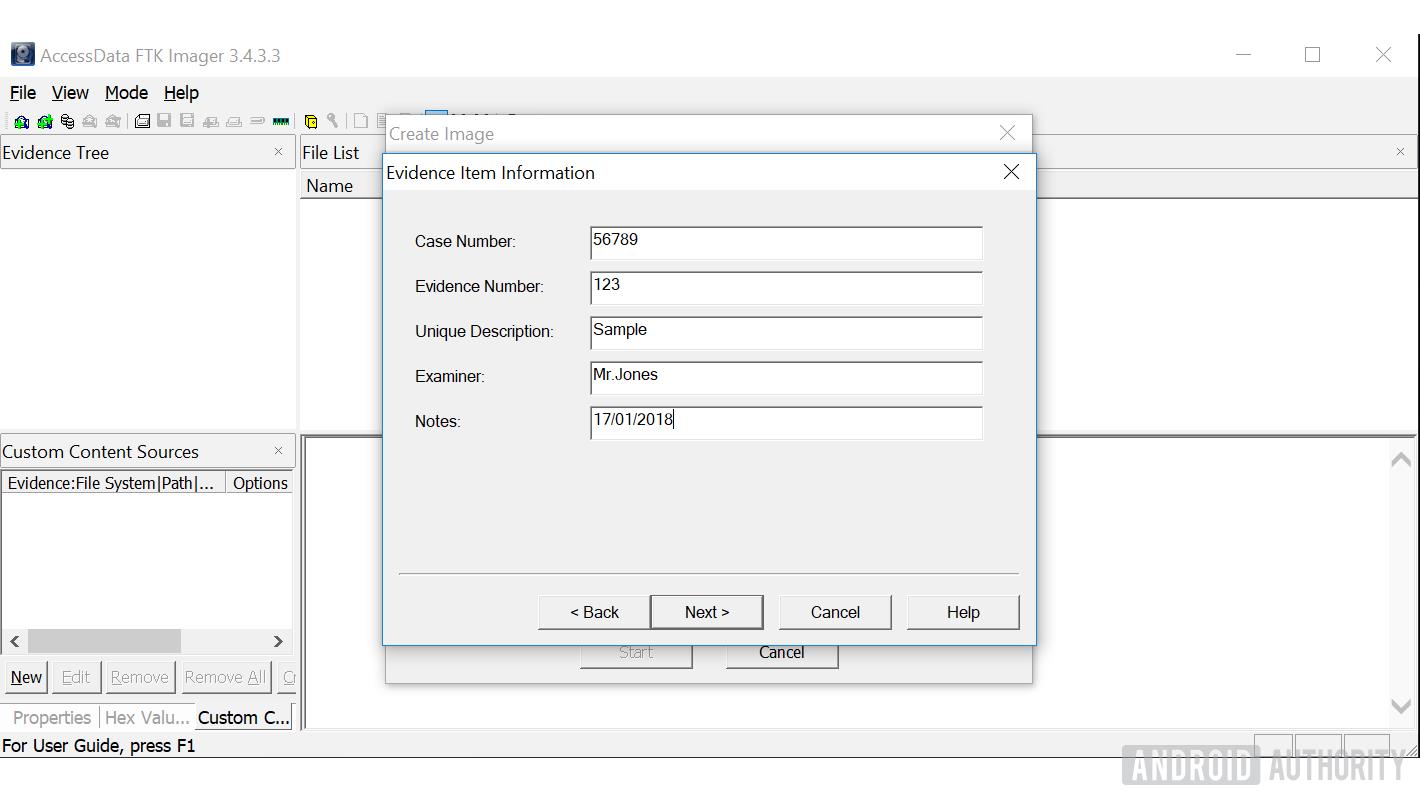
- In the "Select image destination" segment browse to an appropriate folder to save the image.
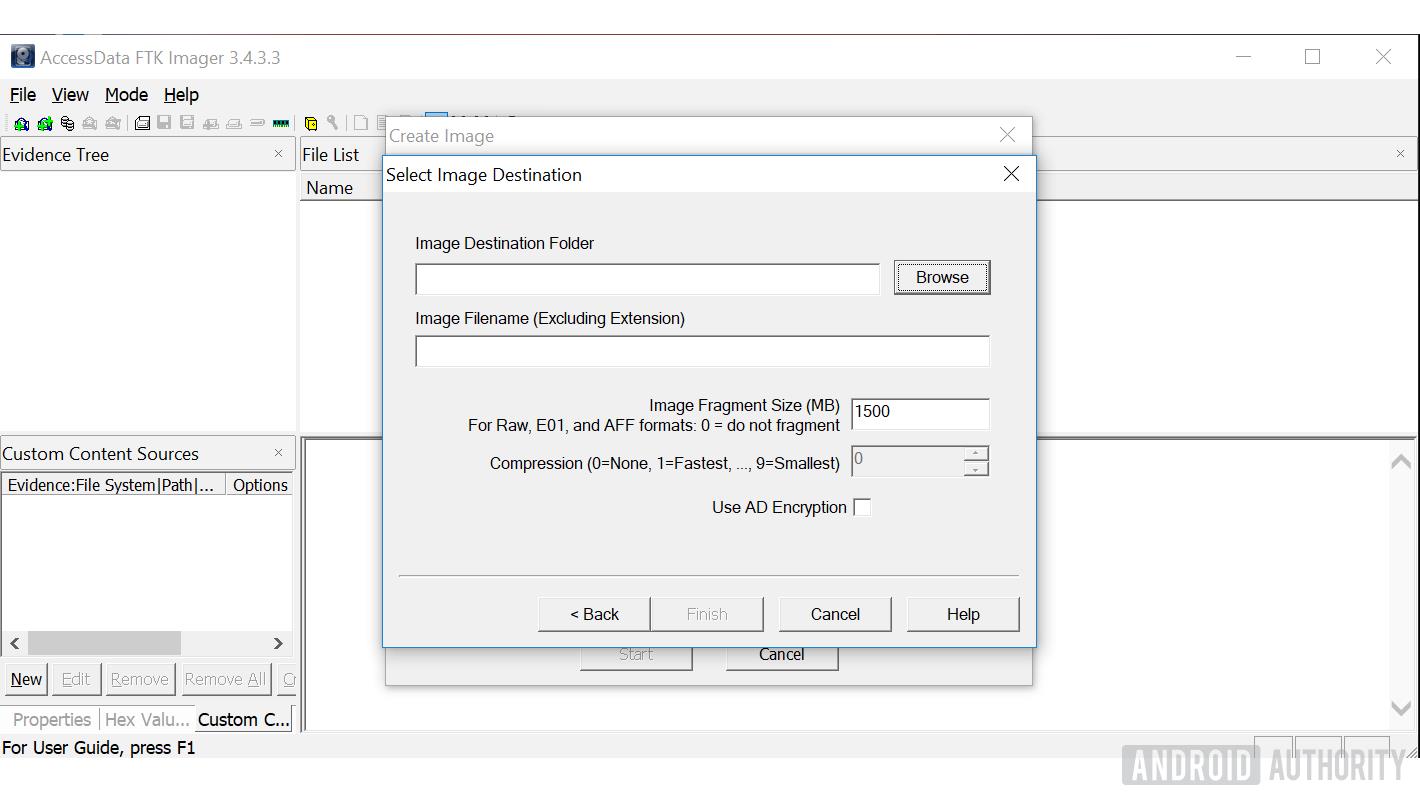
- Make sure 'Verify image…' is ticked before hitting 'Start' to begin the imaging process.
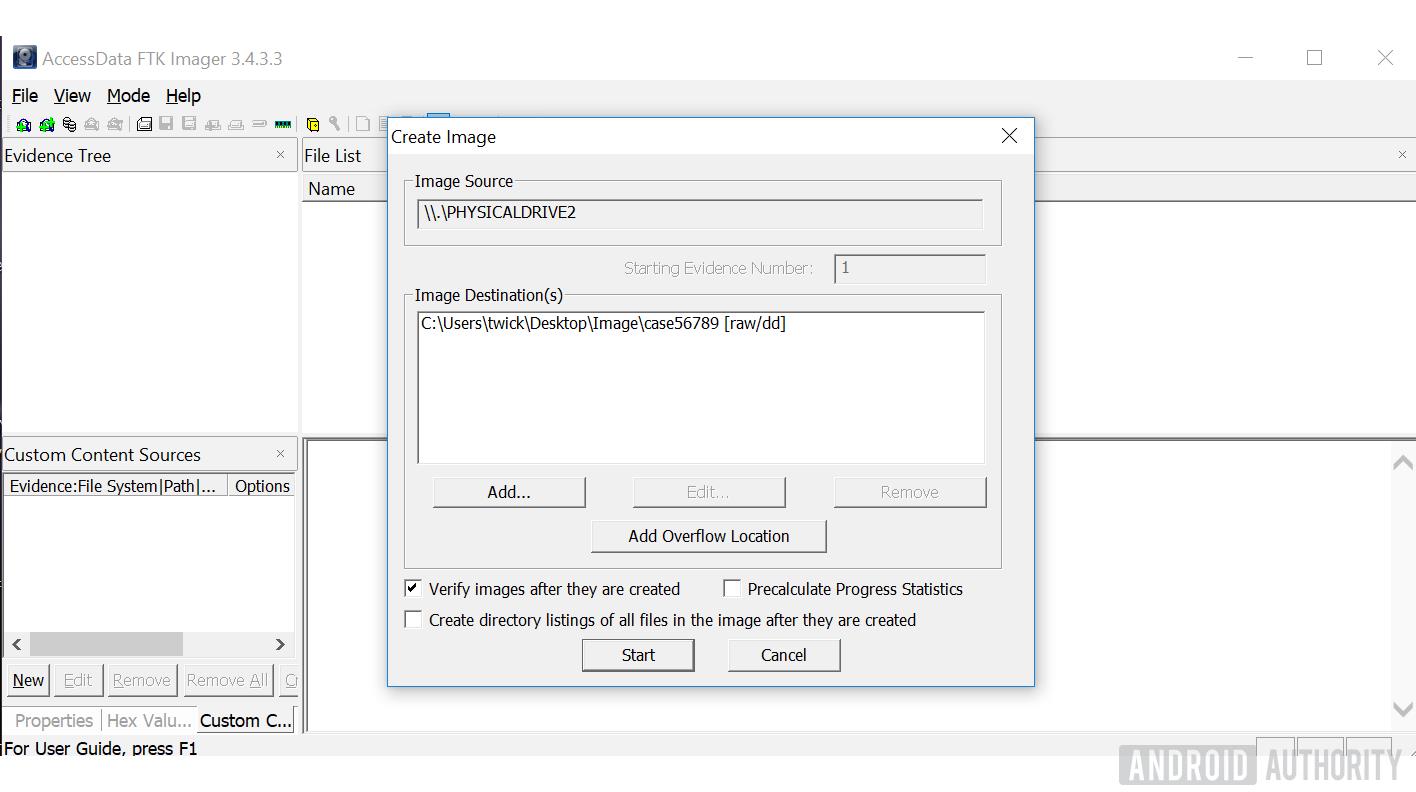
- The imaging process will begin. The length of the process will depend on size of data stored.

- After the process is complete a window will pop up with matching hash verification results if the acquisition was successful.
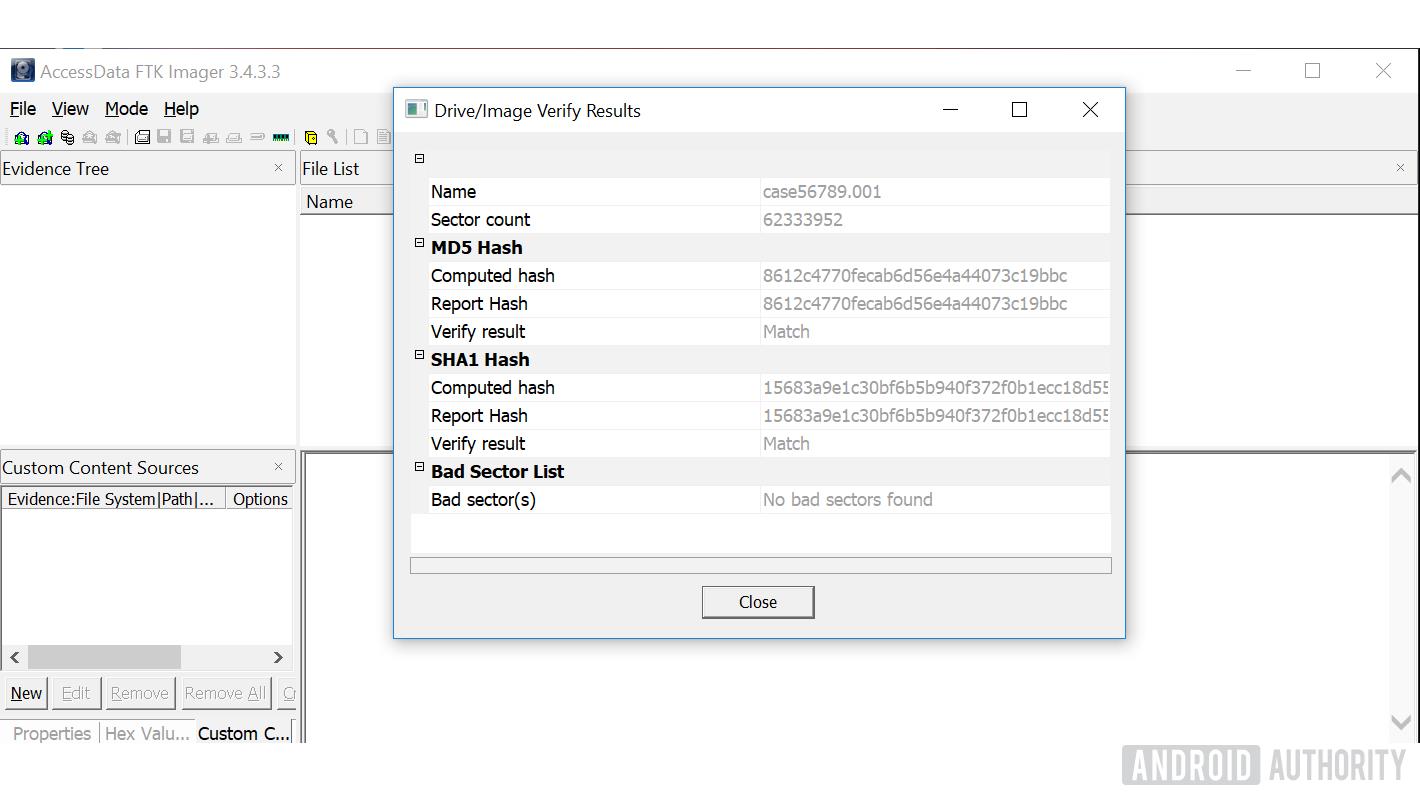
Wrap-up
Acquisition is just the beginning. Afterward, the imaged files can be loaded into data analysis software, allowing examiners to browse through visible and deleted data present on the device. Data acquisition is an essential component of Android forensics and needs to be free from inaccuracies to ensure none of the data is manipulated during the acquisition process.
It also allows you to recover deleted or damaged files, or to remove malware without using the original device, and therefore without fear of further corruption. Knowing how forensic analysts work can also reveal just how susceptible your data is, even after it has been deleted.
Have you ever had to work with corrupted data, or even with sensitive data in some kind of criminal investigation? Did you use a copy? Let me know in the comments below!
*Feature written by Thomas Wickens – Wickens has a background in forensic computing and security, and years of experience as a tech writer.*
from Android Authority http://ift.tt/2BCDofG
via IFTTT
Aucun commentaire:
Enregistrer un commentaire